IAM for Agentic, API, and Workload
The Non-Human IAM to replace manual and insecure access to service accounts, API keys, tokens and other NHIs across Cloud, On-Prem and SaaS environments.

Non-Human Identities Challenge
Growing secrets, Growing risks.
More workloads, More work.
With the adoption of AI, automation, and interconnected integration, the growing presence of non-human identities brings more security risks. The engineering teams' burden of adopting and managing these operations is also increasing.

Proactively eliminate security risks and manual work.
Over the past 20 years, people have transformed their identity and access control into modern approaches based on policies, MFA, SSO, and Zero Trust. It's time to do the same for your non-human.



Enterprise Architecture
Deploys Where You Deploy Software
Don’t let the tools you use drive where you run your distribution applications. xIAM provides support for on-premises, SaaS, and cloud service providers (CSPs).

Proxy Approach
A collection of components deployed in your environment that handle identity and authentication functions for your workloads. The primary component in this system is the Agent/Proxy, which collects workload identity and other contextual information.

API Approach
When you can’t deploy Agent/Proxy, your turn to our feature-rich set of APIs that enable full automation of the xIAM. xIAM APIs can be used in parallel with xIAM Agent/Proxy to enable a more integrated solution.
The Central Access Orchestration Layer
xIAM is committed to building a first-class ecosystem, compatible with a range of heterogeneous environments, and seamlessly integrated with major IaaS, PaaS and SaaS, Trust and Credential Provider, IdP, EDR, SIEM, etc. We will continuously expand according to your use case needs.
Designed for Self-Hosted, Made for the Edge
Your Edge can be deployed flexibly in single cloud, multi-cloud, on-premises DC, or IaC environments. It runs in a variety of heterogeneous environments, providing you with complete control over your data, gateway visibility, and on-demand network coverage.





Workloads and Devices
The Agent/Proxy support a range of operating systems and runtime environments, deploying alongside your apps(workloads). They enforce device restrictions and posture checks through integration with EDR.
Applications and Services
Allows you to configure fully customized HTTP and TCP applications. Continuously integrate with modern APIs and services (such as third-party SaaS APIs, API gateways, databases, and data warehouses), enabling you to connect easily.

Fine-grained control
Based on plugins and DSL rule engines. Agile support for your business development needs, both foreseeable and unforeseen, like Lego.
Routing
SSL & TLS
AuthN/Z
AI / LLMs
Logs
More...
Application Identity Verification
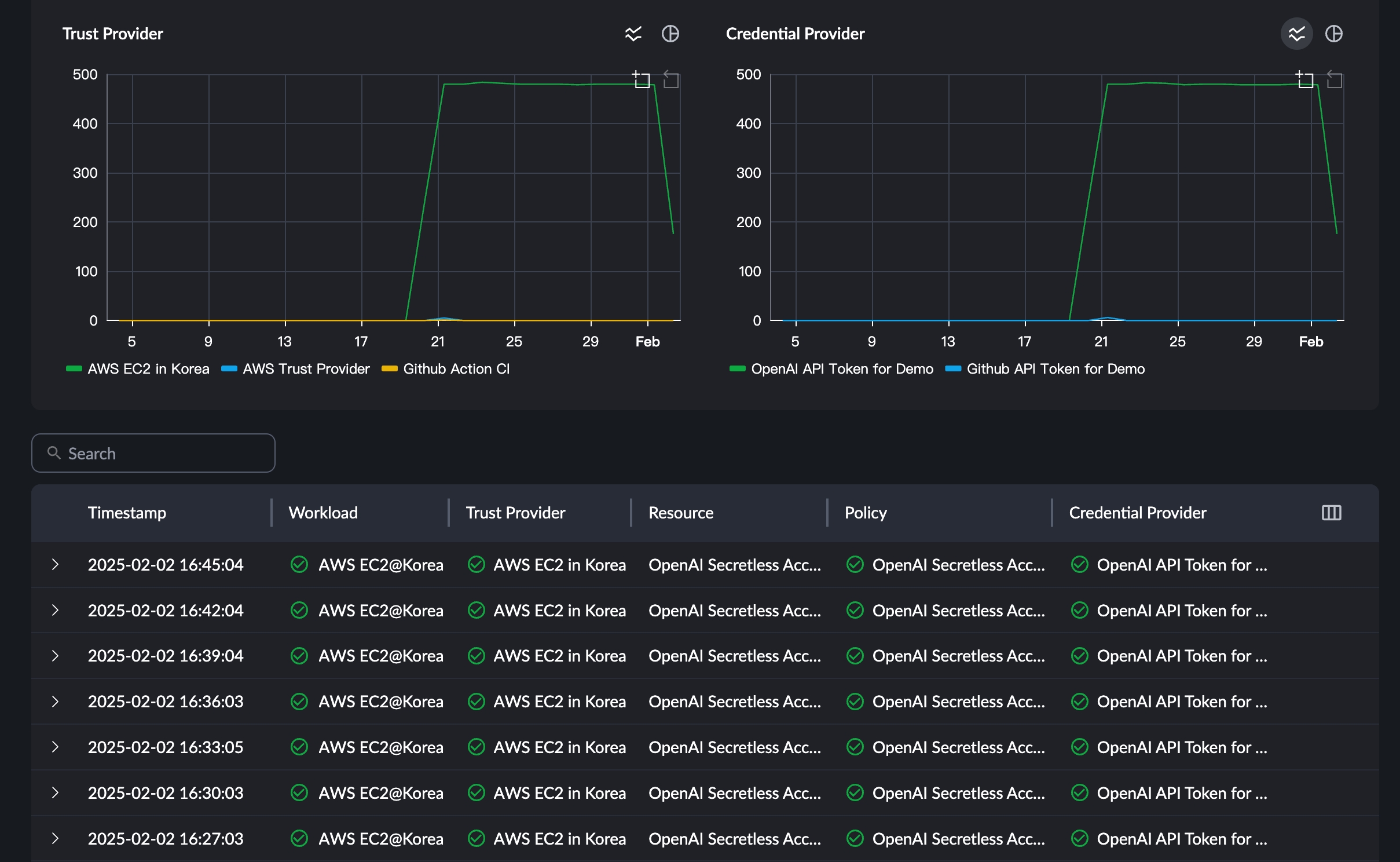
Trust Providers allow AxisNow to verify identities without the need for provisioning credentials or secrets.
Application (workload) identity verification is a core function. Only your own workloads — running in safe environments and communicating over secured connections — can use your APIs and backend resources.
xIAM integrate with AWS metadata, GCP Workload Identity Federation, iOS App Attest / DeviceCheck and Google Play Integrity etc to provide the most comprehensive attestation



Runtime Secrets Protection
Credential providers (CPs) are systems that provide various types of access credentials, like OAuth tokens, API keys, or username and password pairs.
The credential providers delivers secrets “just-in-time” to the app only at the moment they are required to make an API call, and only when the app and its runtime environment has passed attestation. This ensures that sensitive secrets cannot be extracted from the app package or via MitM attacks. Developers also do not need to hardcode secrets. They can never be leaked.







.svg)
.svg)